I am currently working with the following configuration for a custom image:
- Ixora Board v1.2
- Apalis-iMX6
- TorizonCore 6.1.0 Build 1
- Developing a Qt application using the Visual Studio Code Extension for Torizon
My application is using an SD Card as file storage, so I need to expose the port to the container.
Using the lsblk command, I can see the SD card is identified as /dev/mmcblk0p1
Attempted Method 1
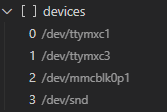
So my first attempt was to add this device to the configuration on VS Code, like so:
Then, inside my application container, I tried running the command mount /dev/mmcblk0p1 /mnt, to get the following output:
![]()
Using sudo prompts me for a password, which I do not know since it doesn’t seem to be the same one set on TorizonCore.
Attempted Method 2
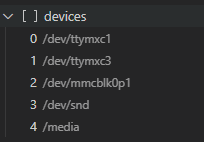
I see that TorizonCore automatically mounts SD Cards in /media as a sub-folder.
![]()
So, similarly to Method 1, I tried to add /media to the configuration on VS Code, assuming it could also expose all the sub-folders:
By doing so, if I deploy and start this container, I get the following error:
Error (525) - Docker exception: 500 Server Error for http://127.0.0.1:37959/v1.41/containers/a550953a8e9d5e7a65aa8fccec9565cc5901c5105b4d8129c18de153567353d2/start: Internal Server Error ("error gathering device information while adding custom device "/media": not a device node")
I used a similar method as Method 1 to access serial ports and it worked correctly, but not for the case of the SD Card.
I’m not sure if I missed a step or if there’s another method I’m unaware of.
Thanks in advance,
Anthony