Hello everyone,
I’m working on a project using Yocto Scarthgap on a Verdin iMX8MP board. I’ve enabled secure boot via the meta-toradex-security layer by inheriting the tdxref-signed feature to extend the chain of trust all the way to the rootfs.
I’m now integrating OTA updates with Mender and wondering if it’s possible to update only the rootfs (without touching the fitImage), without triggering errors related to initramfs or dm-verity. Does anyone have details on how this works in this setup?
From what I understand, the initramfs computes the rootfs hash at boot from the hash tree in the rootfs partition (via .ext4.verity) and compares it to the expected hash metadata (generated during build and stored in the rootfs). If that’s correct, it should allow updating just the rootfs partition without rebuilding the fitImage. Is the rootfs signed in the same way as the fitImage?
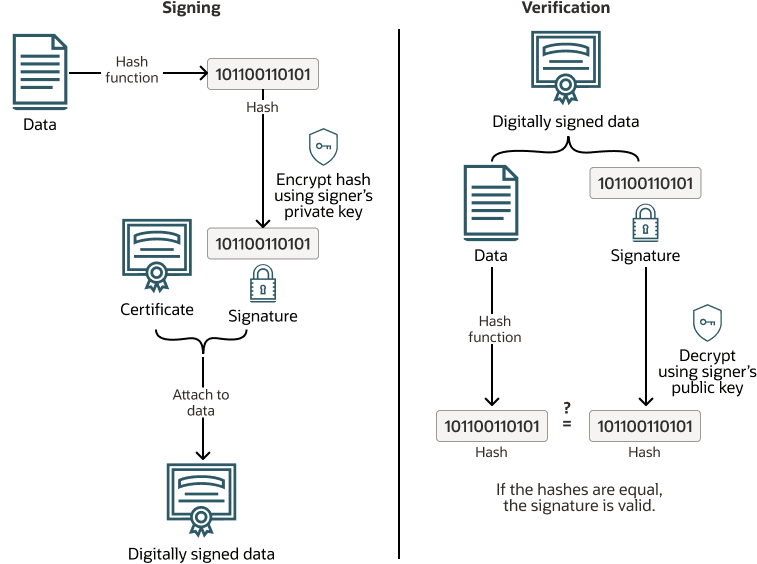
Finally, does secure boot with meta-toradex-security work like in the attached image (sboot-signverify.jpg)? Does the signing/verification follow this scheme?
Thanks in advance for your feedback and experiences!
Best regards,
Stan