Hi @jeremias.tx,
Thanks for the additional feedback and questions to understand each other.
You’re doing an offline update right after flashing an image with TEZI. Is there a reason you don’t just flash the image with the updated content from the start?
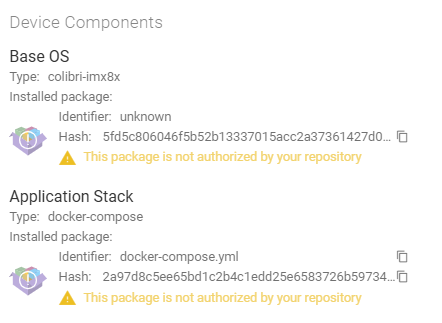
At the moment we are exactly doing what you mention as “flash the image with the updated content from the start”, but the TEZI image is something unknown to Torizon (it is coming directly as output from TCB) and in Torizon I see the following warning “This package is not authorized by your repository” for both Base OS and Application Stack, which works but it is not ideal.
Wait, have you reported this behavior to us before?
I think I’ve already talked about this topic with some of your colleague in the past, but it is not a major issue and my understanding is that is because the TEZI image is unrelated from Torizon Platform and not signed/authorized with its KPI.
So you flash an image with TEZI “without offline updates”, what does that mean? The image you flashed isn’t configured for offline updates? Or something else?
I was meaning our current process of 1) flashing a factory firmware as TEZI image with TEZI and then 2) after production, online-updating. At the moment we don’t use offline updates in our processes yet, we may enable it in future.
Then, you say the “factory firmware” are you talking about the Lockbox now?
No, with “factory firmware” I mean the current way of factory programming a TEZI image with TEZI. Sorry for the confusion, but the initial question was in the perspective of switching to Lockboxes as “factory firmware”, something different from the current process.
Finally about the “Not authorized in this repository”. You’re seeing this on our Web UI? Or what are you seeing exactly?
As in the picture above, it is seen in the Torizon Cloud UI. Our TEZI image used as factory firmware are still relatively old, I am not sure if something changed on this with TCv6.
Cheers,
ldvp